
|
http://www.dmst.aueb.gr/dds/pubs/jrnl/1999-IMCS-Soft-Risk/html/soho.html This is an HTML rendering of a working paper draft that led to a publication. The publication should always be cited in preference to this draft using the following reference:
|
According to the MCB Copyright policy ``authors are free to post their own articles on their Web site after they have been published in an MCB journal. This is subject to acknowledgement of first publication details and inclusion of a link to Emerald’s home page http://www.emeraldinsight.com.''
The pervasive use of information technology in enterprises
of every size and the emergence of widely deployed ubiquitous
networking technologies have brought with them a widening need
for security. Information System security policy development must
begin with a thorough analysis of sensitivity and criticality.
Risk analysis methodologies, like CRAMM, provide the ability to
analyse and manage the associated risks. By performing a risk
analysis on a typical small enterprise and a home-office setup
we identify the risks associated with availability, confidentiality,
and integrity requirements. Although both environments share
weaknesses and security requirements with larger enterprises,
the risk management approaches required are different in nature
and scale. Their implementation requires co-operation between
end-users, network service providers, and software vendors.
Keywords: risk analysis, enterprise, home, security, recommendations
Advances in networking technology, the explosive growth of the
Internet, and the liberalisation of telecommunication markets
increasingly allow small businesses and private individuals to
reap the benefits of sophisticated networked computer applications.
Examples of such applications include electronic commerce, teleworking,
multimedia communication, information access, and entertainment.
Unfortunately, the realisation of these applications is often
hampered by insecurities typical to open networks: messages can
be intercepted and manipulated, the validity of documents can
be denied, and personal data can be illicitly collected. Large
enterprises can typically design and implement security policies
for their data networks (Kabay 1996) and implement them using
technologies such as virtual private networks and firewalls.
However, the use of networked information systems within small
enterprises and modern home-office environments can be the source
of serious security problems, because such enterprises typically
lack the technical expertise and resources to create and maintain
a suitable level of security.
The adoption of a systematic approach and a standard methodology
for the establishment of a baseline on security practices for
the emerging ubiquitous networking environment allows the stakeholders
of this environment (users, network service providers, equipment
and software vendors) to evaluate the required security level
and take appropriate strategic and tactical decisions.
Risk Analysis, an orderly process adapted from practices in management, is a valuable methodology for every attempt towards the establishment of a secure Information System (IS), as it addresses two important issues (Eloff et al. 1993):
In this paper we apply a risk analysis methodology on representative
examples of the emerging ubiquitous networking environment, analyse
the associated risks, and provide and overview of approaches for
risk management. The paper can serve as a rough roadmap marking
the areas where the peculiarities of the new environment require
novel approaches from end-users, vendors, and network service
providers.
One can not reasonably develop security policies and procedures without clearly understanding the systems that must be protected and how valuable they are to the enterprise. In addition, one must determine the probability that the assets will be threatened. Therefore, the objective of risk analysis is to identify and assess the risks to which the IS and its assets are exposed in order to select appropriate and justified security safeguards. The analysis of risks is performed in five stages (ISO/IEC/JTC1 1996):
Assets are the elements of an IS that possess a value. A security
incident that will affect an asset will also have an impact on
the owner of the asset (i.e. the organisation, the enterprise,
or the individual). Assets are valuated according to the impact
of a probable asset impairment. Threats need to exploit a certain
vulnerability in order to cause a security incident. Therefore,
threats, vulnerabilities, and impacts should be combined together
to provide a measure of the risk an IS is exposed to. The implied
conceptual model (CEC 1993) is given in Figure 1.
The risk analysis methods database developed within the CEC/INFOSEC Programme (CEC 1993b) contains more than seventy risk analysis methods. In our analysis we chose CRAMM, the United Kingdom Central Computer and Telecommunication Agency (CCTA) Risk Analysis and Management Method, for the following reasons:

The CRAMM software tool provides automated selection of countermeasures.
CRAMM countermeasures are also ascribed to policy statements that
constitute the security requirements of the system and form the
basis for the development of a security policy.
The CRAMM methodology (UKCCTA 1996) involves three stages:
Our study has been based on two exemplary scenarios. The first
one concerns a small enterprise and the second a home user that
maintains a home-office environment.
The first scenario represents a modern small enterprise that makes
use of advanced networking technology, while retaining a basic
computing infrastructure. The infrastructure of the enterprise
includes three PCs and a printer connected via an ethernet local
network. Two of the PCs are used as workstations, whilst the third
one is used as a server. The latter also hosts a Web Server. An
ATM line connects the enterprise with a Network Service Provider
that provides Internet connectivity.
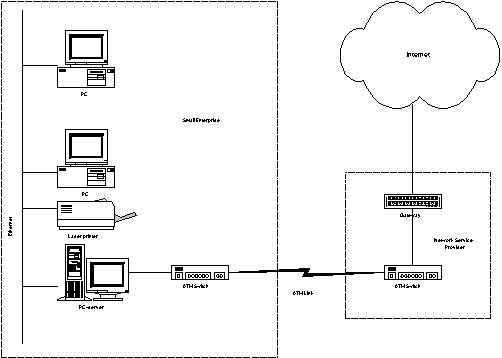
The business functions of the enterprise that involve the use of computing facilities are the following:
The second scenario represents the case of a home user who uses ISDN technology for both entertainment and business purposes. The equipment used includes two PCs and a printer connected to a local ethernet network and through an ISDN line to a Network Service Provider who provides Internet connectivity. The ISDN line gives the user the ability to use the same connection for a video phone, a fax, and a conventional telephone. The basic activities in this setup include:
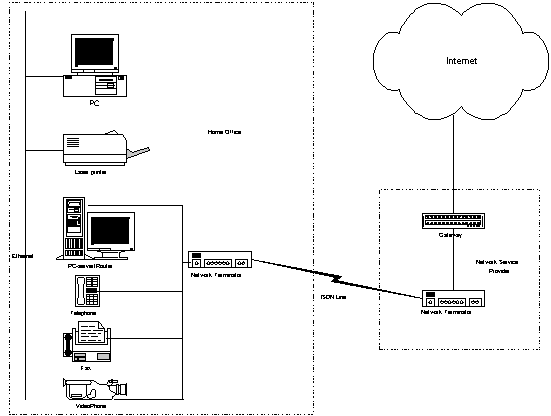
After performing the risk analysis of the two scenarios using
the outlined methodology, we found that although different in
size the small enterprise and the home-office face a similar level
of risk. This can be justified if we consider the risk analysis
process. Risk is calculated as a combination of the value of assets
(estimated according to the impact an asset impairment may have),
the level of threat, and the level of vulnerability. The threats
are common in both cases and result mainly from the use of open,
high speed networks, though physical threats (e.g. fire) have
not been ignored. The level of vulnerability is similar in both
cases with the home-office case being more vulnerable because
of the use of the same facilities for both work and entertainment.
The only significant differences have been identified through
impact assessment, where it appears that the small enterprise
has a greater need for availability, confidentiality and integrity
for the purpose of conducting electronic commerce (Warren and
Furnell 1998). However, the home-office also requires a high level
of protection since all professional activities are conducted
through the same computing facilities. The following paragraphs
provide an overview of the availability, confidentiality, and
integrity requirements that we identified.
Large enterprises may have several computing installations and
produce a wide range of products, so the unavailability of a certain
installation can be overcome by activating other resources. In
contrast to large enterprises, home-offices and small enterprises
have a greater dependency on their IT systems since their owners
typically have no other source of income or spare IT resources.
Unauthorised disclosure of information is a significant threat
in both scenarios. Especially in the case of a small enterprise,
electronic commerce data exchanged is quite sensitive (e.g. credit
card numbers) and often protected by law. In addition, it is important
to protect the privacy of the employees of the small enterprise,
the home user, and their clients.
Integrity issues are quite important especially considering the
application of electronic commerce. Modification of e-commerce
data may result in high financial losses. A wide range of potential
perpetrators may be interested in deliberately modifying financial,
commercial, and EDI data. These may be dissatisfied or malevolent
customers, crackers, or aggressive competitors.
Tables 1 and 2 show the highest risk values in the two case scenarios.
The evaluation of risks follows a scale of 0-7 where 6 and 7 mostly
apply in safety critical systems. CRAMM estimates risk values
for every combination of asset impact, threat, and vulnerability.
The list of all risks is several pages long and is considered
beyond the scope of this paper.
| Small enterprise | ||||||||||
| Home-office | ||||||||||
| Unavailability: 15M-15 min., 1H-1 hour, 3H-3 hours, 12H-12 hours, 1D-1 Day, 2D-2 Days, 1W-1 week, 2W-2 weeks, 1M-1 month, 2M-2 months.
| ||||||||||
| Small enterprise | ||||||||||||
| Home-office | ||||||||||||
| B-loss of data since last back-up; T-total loss of data; O-disclosure to outsiders;
SE-small scale errors; WE-widespread errors; DM-deliberate modification; In-insertion of false message; Or-repudiation of origin; Rc-repudiation of receipt; Nd-non-delivery; Mr-mis-routing; Tm-traffic monitoring. | ||||||||||||
The main conclusions resulting from our risk analysis review are the following:
The aforementioned conclusions highlight the necessity for risk
management. This is performed by determining the security requirements
and selecting appropriate countermeasures.
Managing risks may follow three strategies: risk reduction, risk
transfer, and risk acceptance. Accepting risk means that although
one is aware of it he or she prefers to accept the consequences
instead of applying countermeasures. This applies in the case
where the cost of countermeasures is significantly higher than
the impact of a potential security breach. An example of risk
transfer is insurance and applies in particular to physical assets
(e.g. computers). Note that in most cases the insurance contract
covers the replacement value of equipment and not the value of
the data contained or processed by it. Finally, reducing risk
could be achieved by means of reducing threat, reducing vulnerability,
reducing impact, or recovering from threat occurrences.
CRAMM provides a list of recommended countermeasures that reduce
risk in any of the ways mentioned above. A security expert may
select those that provide the highest effectiveness with the lowest
cost. As a result of the high risk values that we identified
in the previous section, we compiled a lengthy list (a few hundred
items) of requirements (Dubois and Wu 1996, Rohm et al 1998) and
countermeasures to be applied. The most important requirements
are abstracted in Table 3. The cost of implementing the countermeasures
is obviously beyond the abilities not only of a home-office environment,
but of a small enterprise, as well.
| Requirement | Possible Solution |
| User IDs All users should be allocated an identifier (user ID). | The operating system should ensure that access is only granted with the provision of an ID and a means of authentication (e.g. password, smart card). |
| Password management Passwords should be difficult to guess. They should be kept in a one way encryption form; they should change at least once every six months; they should be transmitted in an encrypted form; they are not to be stored in macros or function keys. | Current practice in PC-based systems does not comply with the above requirements (e.g. passwords are often stored in macros to be used for ftp or telnet sessions). The problem could be addressed by means of using proactive password checkers, password generators and the provision of relevant services by the operating system. Smart cards provide an alternative authentication method, but appropriate infrastructure is needed (e.g. inexpensive and easy to use card readers, standardisation in smart card technology). |
| Logical Access Control The owner of a file or a program should be provided with the facility to specify who is allowed to access the file or program (Discretionary Access Control). All files and directories should have an owner. | Incorporate Discretionary Access Control in PC-based operating systems and networking software. |
| Access Control Access rights should be reviewed at regular intervals. Inactive accounts should be locked. | Automate the review of access rights based on checklists and procedures available in certified Security Handbooks. |
| Auditing Tools A range of facilities for keeping and analysing Audit Logs should be provided. Audit logs should be available in database format and reports should be provided in word-processing format. | Provision of easy to use audit tools, with predefined auditing profiles and customisation options. Quite often the difficulties of managing huge audit logs force users not to activate auditing. |
| Investigation of Incidents When incidents are detected or suspected they must be investigated in a thorough manner. | Development of Incident Reporting Schemes (IRS). General purpose CERTs will not be able to address the increasing needs for incident response in the future. The development of sector-specific IRS appears as a more promising solution. |
| System Security Acceptance Criteria Acceptance criteria should be established against which suitable test should be carried out prior to acceptance of a system as providing the required level of security. | Certification of software by accredited certifiers. |
| Software Integrity Checks Breaches of software integrity should be detected and prevented. | Several security packages offer file integrity checking. These facilities could be integrated into the operating system. |
| Detection of Malicious Software Any malicious software should be detected, identified, isolated, and removed. Users have to deal with attacks from malicious network applets which can cause many problems, such as denial of service, invasion of privacy, and annoyance. | Anti-virus tools and good practice rules. All anti-virus tools must be kept up-to-date. Digital signature techniques can be used for the verification of signed applets (e.g. Microsoft's Authenticode technology) (Gritzalis et al 1999). |
| Security of Network Services The service provider's contract should formally define the security issues for the Network Service. | Standard contracts and terms of business relating to security issues can be standardised by relevant bodies and applied uniformly across all network service providers. |
| Mutual Authentication All communicating entities should be authenticated. | Public-key infrastructure (PKI); application of cryptographic and authentication protocols for implementing Virtual Private Networks |
| Network Access The flow of traffic to and from external networks should be controlled. | Integrate firewall functionality and auditing facilities into router and gateway software. |
| Message Origin Authentication The origin of a message should be authenticated. | Research has provided several non-repudiation techniques that need to be standardised and employed. Digital signatures, based on public-key cryptography, are widely considered as crucial. Legal and regulatory issues have to be addressed by governments leading towards an integrated framework for secure network transactions. |
| Operational Change Procedures Management responsibilities and associated procedures are necessary to ensure satisfactory control of all changes to equipment, software, and procedures. | Minimise the security vulnerabilities that can be introduced by user modifications. Encourage the use of certified Security Handbooks and Checklists. |
| Operating System Changes When such changes occur the security of the system should be reviewed to ensure that the changes have not introduced any adverse affects. | Include security checks in the installation procedures of operating systems updates. Provide a certification framework for operating system upgrade procedures. |
| Access to Manager Accounts The system administrator account should not be used for day-to-day operations. | Design network and operating system administration procedures to minimise the need for a system administrator account. |
| Data Backups Backups should be taken of all essential business data; backup should be stored in a separate location; it should be possible to re-create data lost since the last backup. | Provision of backup services by network service providers; for example, user data backup can be performed over a high-speed network. |
| Security Awareness Staff should be aware of IT security issues. | Small enterprises cannot afford seminars and training programs on security, but at least users should be aware of the threats and of the basic security requirements. |
| Security policies An IT Security Policy should be documented. | Use of baseline or standard security policies developed by associations, standardisation bodies and other trusted organisations. |
| Incident Handling Security incidents should be detected and investigated thoroughly. | Development of sector-specific Incident Reporting Schemes. Some types of incidents could be automatically reported and managed by the network service providers. |
Considering the lack of resources, the lack of security provisions in PC-based systems, and the currently low security level of Internet technologies, there is no way a small enterprise or home user can afford an adequate level of security today. It is thus necessary to advance the state of the art to provide a secure baseline for small enterprises and home users. This will involve vendors, network service providers, government, and private organisations.
System Software Vendors Security services (e.g. authentication, discretionary access control, etc.) should be incorporated into PC operating system software. However, if these offer a wide range of security options it is obvious that a non-expert will be puzzled. Therefore, specific "security profiles" could be offered so that the user can select the profile that is closest to their needs. When selecting a profile the corresponding security policy will be automatically employed.
Network Service Providers They may offer a wide range of security services, such as anonymity, encryption, back-up, incident reporting, and data recovery services. Many of these services can be provided with minimal user intervention if they are standardised and tightly integrated with the networking software.
Third Parties It is absolutely essential to develop and deploy a security infrastructure (including a Public Key Infrastructure-PKI) that will address the needs of small enterprises. In addition, a network of accredited certifiers (Wilsher & Kurth 1996) that will provide security certification services for PC software products would absolve users from difficult to perform security tests of off-the-self software products. Additionally, non-expert users will benefit from "Security Handbooks" that will contain security policies, security procedures and checklists.
Users In most cases measures that transfer risk or enable
recovery from security incidents require less resources and are
easier to apply. Two measures of this kind, insurance and back-up,
have always provided a good level of security. Insurance may cover
losses in equipment and backup data losses. Backup data should
have the same protection as active data, should be stored in a
different location, and the restore procedure should be tested
and be known by all users. Given a security infrastructure, the
emerging network technologies could allow WAN-based backup services
to be provided. Passwords are thought as the weakest point of
attack in almost every system. Good password management practices
provide a highly important defence safeguard in an IT system.
The advent of the Information Society brings up new business opportunities for small and medium size enterprises (SMEs) and promotes new forms of work organisation. Moreover, growth and employment largely depend on the proliferation of teleworking and the use of telematic services by SMEs (Bangemann committee 1994).
The Risk Analysis review performed for the purposes of this paper has shown that small enterprises and home offices currently operate in high risk environment. In addition, current security infrastructure and business practices do not allow for effective risk management. Consequently, the lack of a secure environment for small enterprises and home offices canbe expected to hinder their development. Moreover, recent security surveys (Hinde 1998) show that the rate of security breaches has increased in the last few years. The latest survey conducted by the UK Audit Commission reports that 45% of organisations surveyed had suffered from computer fraud and abuse - up from 36% three years ago (UK Audit Commission 1998).
This paper provides a rough roadmap for the establishment of a
secure environment for small enterprises and home offices. The
proposed solutions are based on novel approaches to security management
practices, and imaginative use of sophisticated technologies.
Their deployment requires tight co-operation between all stakeholders
in the emerging network infrastructure: end-users, network service
providers, and software vendors.
Commission of the European Communities (CEC 1993) Glossary of information systems security. DGXIII, INFOSEC Programme/S2001.
Gritzalis S., Aggelis G., Spinellis D., (1999) Architectures for Secure Portable Executable Content", Internet Research Journal, Vol.9, No.1, pp. 16-24, MCB University Press.
Hinde S. (1998) Recent Security Surveys. Computers and Security, 17(3):207-210.
ISO/IEC/JTC1 (1996) Information Technology - Security Techniques - Guidelines for the Management of IT Security, GMITS. ISO/IEC DTR13335.
Kabay E. (1996) The NCSA Guide ot Enterprise Security: Protecting Information Assets. McGraw-Hill.
Rohm A., Pernul G., Herrmann G., (1998) Modelling secure and fair electronic commerce, Proceedings of the 14th Annual Computer Security Applications Conference, pp. 155-164, IEEE Computer Press.
UK Audit Commission (1998) Ghost in the Machine - an Analysis of IT Fraud and Abuse. The Audit Commission, UK.
Wilsher, R. G., Kurth, H. (1996) Security assurance in information systems. In Sokratis K. Katsikas and Dimitris Gritzalis, editors, Information Systems Security: Facing the information society of the 21st century, pages 74-87. Chapman Hall.
Biographical Information
Dr. Diomidis Spinellis
holds an MEng in Software Engineering and a PhD in Computer Science
both from Imperial College (University of London, UK). Currently
he is lecturing at the Department of Information & Communication
Systems, University of the Aegean, Greece. He has provided consulting
services to a number of Greek and international Information Technology
companies and has been involved in several national and EU funded
R&D projects in the areas of Computer Security, Language Engineering,
and Scientific Visualisation. He is the author of more than 40
technical papers and conference presentations. He has contributed
software to the 4.4BSD Unix distribution, the X-Windows system,
and is the author of a number of public domain software packages,
libraries, and tools. His research interests include Information
Security, Software Engineering, and Programming Languages. Dr.
Spinellis is a member of the ACM, the IEEE, the Greek Computer
Society, the Technical Chamber of Greece, and a founding member
of the Greek Internet User's Society. He is a co-recipient of
the Usenix Association 1993 Lifetime Achievement Award.
Spyros Kokolakis received
the B.Sc. degree in Information Systems from the Athens University
of Economics and Business (AUEB) in 1991. He is now a research
student in AUEB, working on Information Systems Security. His
current research interests include the development of an Information
Systems Security Analysis and Design methodology, information
security models and security policies and metapolicies.
Dr. Dimitris Gritzalis
holds a BSc (Mathematics) from the University of Patras, Greece,
an MSc (Computer Science) from the City University of New York,
USA, and a PhD (Informatics) from the University of the Aegean,
Greece. Currently he is an Assistant Professor with the Department
of Informatics of the Athens University of Economics and Business
(AUEB), Greece, and a Senior Researcher with the University of
the Aegean. His work includes editorship of two international
conference proceedings, and publication of three monographs and
of 35 refereed papers. Dr. D. Gritzalis has been involved in many
research and development projects on information security; most
of them were funded by the EC under the ESPRIT, INFOSEC, AIM,
RACE, ACTS, ETS, ISIS, VALUE and Telematics Administration Programmes.
His current research interests include information security models
and policies, secure healthcare information systems, and privacy.
He is a member of the Data Protection Authority of Greece and
the representative of Greece to IFIP Technical Committee 11 (Security
in Information Processing Systems).